Understanding Cloud Security Posture Management (CSPM) in Depth
Written on
Chapter 1: Introduction to CSPM
Navigating the field of cloud security can be challenging, especially with new solutions emerging each month. To assist those new to this domain, I am launching a series that explores essential cloud security tools, including CSPM, CASB, CWPP, and more. In this discussion, we’ll delve into Cloud Security Posture Management (CSPM) and its effective application.
Why is CSPM Crucial?
If you ask experienced professionals in the cloud sector about their biggest vulnerabilities, misconfigurations are often cited as the primary concern. Research indicates that 65% to 70% of security issues in cloud environments stem from these misconfigurations.
Unintentional (or sometimes deliberate) modifications can expose cloud databases to cybercriminals, while the sheer volume of events occurring each minute can overwhelm cybersecurity teams, making it difficult to discern priorities.
Chief Information Security Officers (CISOs) often struggle to obtain a clear overview of the main risks within their cloud environments, a challenge that escalates in multi-cloud scenarios. Some crucial queries that CISOs typically seek to address include:
- Are we adhering to best practices?
- What does our current security posture look like?
- Will I be alerted to unauthorized activities in the cloud?
- Can I ascertain whether we’ll pass a cloud audit?
- How can I gain insight into our multi-cloud environment?
As I have reiterated multiple times, traditional on-premises controls cannot simply be transferred to the cloud. The cloud lacks a defined perimeter for enforcement, and manual processes will not scale effectively due to the rapid pace of cloud operations. Without automation, security vulnerabilities can remain undetected for prolonged periods.
The Role of CSPM
This is where Cloud Security Posture Management (CSPM) becomes vital. CSPM tools integrate with cloud infrastructures to identify and assess risks. Their primary function is to provide insights into your risk level and compliance with best practices.
Key features of CSPM include:
- Detecting and rectifying cloud configuration issues such as open ports and insecure assets.
- Identifying and cataloging cloud assets.
- Offering a dashboard that highlights cloud risks with a scoring system.
- Evaluating your cloud environment against security benchmarks like PCI, NIST, and CIS.
- Monitoring environments and identifying deviations from established policies.
Understanding CSPM Types
CSPMs generally come in two varieties: those offered natively by cloud providers and those from third-party vendors. Examples of native CSPMs include:
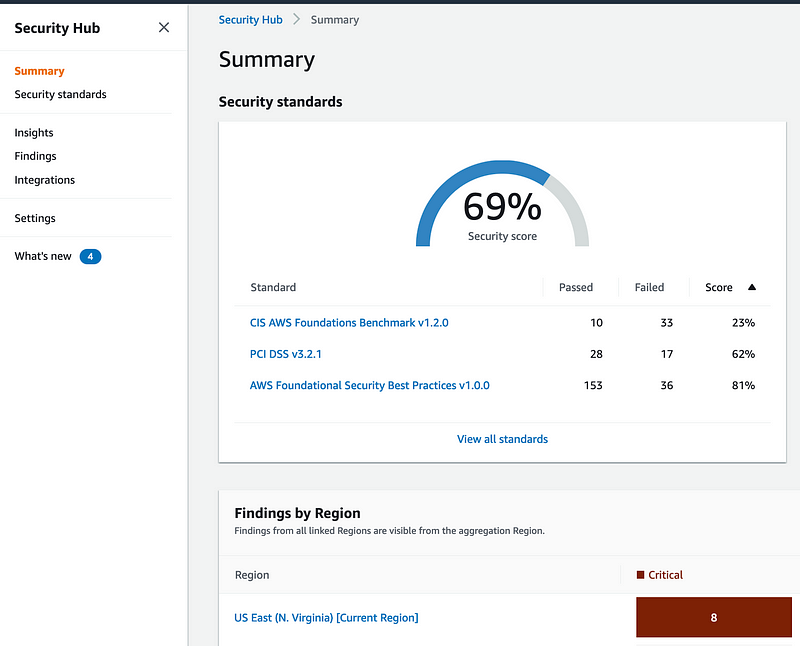
- AWS Security Hub
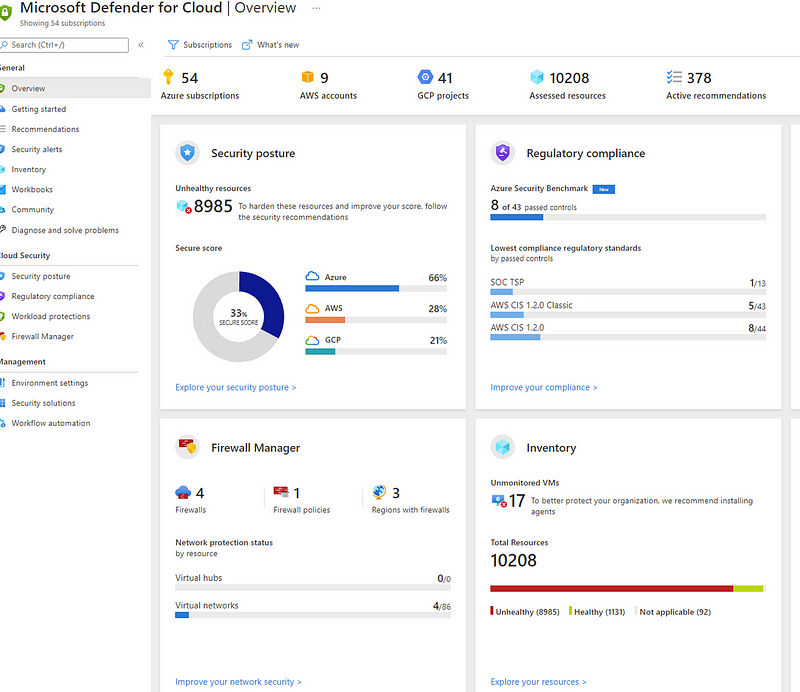
- Microsoft Defender for Cloud
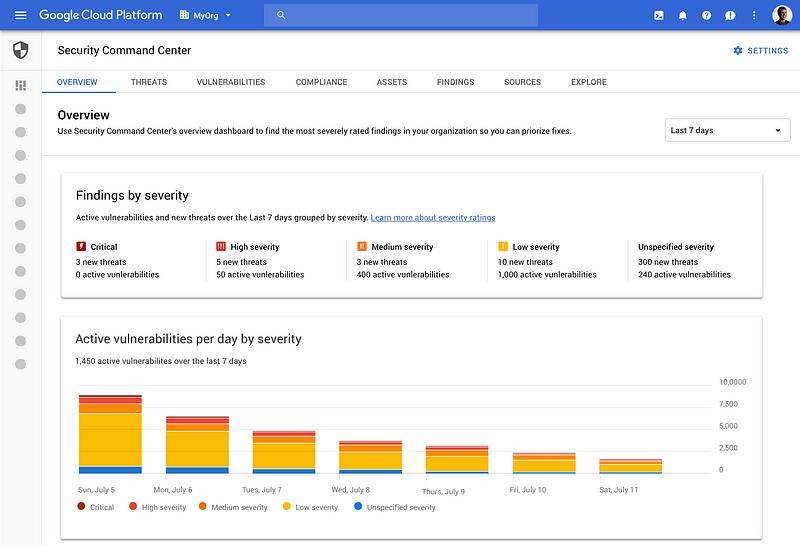
- Google Security Command Center
Additionally, numerous third-party CSPMs exist, which may be better suited for multi-cloud environments. Each option has its advantages and disadvantages, and I won’t endorse any specific vendor.
Tips for Successful CSPM Implementation
Based on my extensive experience with various native and third-party CSPMs, here are some pitfalls to avoid and recommendations for effective implementation:
Common Mistakes
- Treating CSPM as a "silver bullet" that will resolve all cloud security issues. Like any tool, CSPM requires time to learn and adapt for optimal performance.
- Neglecting to optimize alerts. Analyzing and fine-tuning alerts is essential to prevent alert fatigue among security teams.
Key Reminders
- Don’t be alarmed by the initial influx of alerts. Focus on prioritizing critical and high-level alerts first.
- Aim for continuous improvement rather than 100% compliance, as striving for absolute compliance can lead to frustration.
- Delay enabling auto-remediation on day one to avoid disrupting cloud applications; ensure you’ve thoroughly tested the actions it will take.
- Engage your cloud and technology teams in the implementation process to ensure they understand the alerts generated by the tool.
- Integrate with ticketing systems instead of relying solely on email notifications to avoid missing critical alerts.
- Onboard all accounts. A compromised development account can provide attackers with the information necessary to target production environments.
Good luck on your CSPM journey!

Taimur Ijlal is an award-winning information security leader with over 20 years of global experience in cybersecurity and IT risk management within the fintech sector. Connect with him on LinkedIn or through his blog. He also shares insights on his YouTube channel, "Cloud Security Guy," focusing on topics related to Cloud Security, Artificial Intelligence, and cybersecurity career advice.
From Infosec Writeups: The world of information security is ever-evolving. Subscribe to our weekly newsletter for the latest trends, featuring 5 articles, 4 threads, 3 videos, 2 GitHub repositories and tools, and 1 job alert—all for free!
The first video, "What is CSPM (Cloud Security Posture Management)?", provides a foundational understanding of CSPM and its importance in cloud security.
The second video, "Cloud Security Posture Management - CSPM", delves deeper into the functionalities and implementation strategies of CSPM tools.