Ransomware Surge: Analyzing March 2023's Cyber Attack Records
Written on
The Rise of Ransomware Attacks
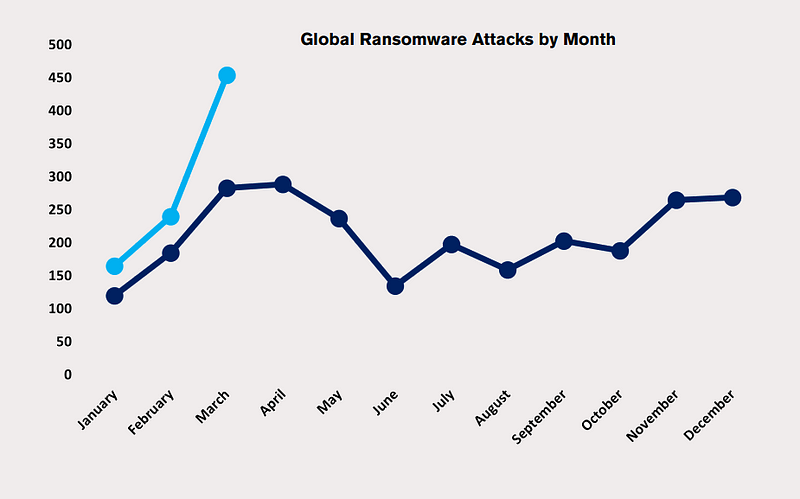
March 2023 proved to be a monumental month for cybercrime, witnessing a staggering total of 459 ransomware incidents. This marked a significant increase of 91% from February and a 62% rise compared to March 2022. According to cybersecurity analysis by NCC Group, the surge was largely attributed to the exploitation of vulnerability CVE-2023–0669 in Fortra’s GoAnywhere MFT secure file transfer tool, perpetrated by the Clop ransomware group.
Within just ten days, this exploit enabled the gang to breach the data security of 130 companies, resulting in unprecedented ransomware attack numbers. The report indicates a growing trend in hacking and data breaches since the start of the year, with the highest levels seen in the past three years. The Clop group surpassed LockBit 3.0 to emerge as the most active ransomware organization, logging 129 attacks, while LockBit followed with 97.
Cyber News: Ransomware Record, Chrome Zeroday, Fortra Findings, SQL & PaperCut Servers Targeted - YouTube This video discusses the recent surge in ransomware attacks, focusing on the vulnerabilities exploited and the impact on various sectors.
Other groups, including Royal ransomware, BlackCat (ALPHV), and Bianlian, also exhibited notable activity during this period. The “Industrials” sector was particularly hard hit, suffering 147 attacks, which accounted for 32% of all recorded incidents. This sector encompasses a wide range of industries, including professional services, construction, aerospace, and logistics.
Sector Vulnerabilities and Geographic Trends
The top three ransomware groups, Clop, LockBit, and Royal, chiefly targeted companies in the industrial sector, with both Clop and LockBit also directing a considerable share of their attacks toward the technology sector. It's essential to understand that while some sectors are more susceptible to these attacks, the nature of ransomware attacks is largely opportunistic.
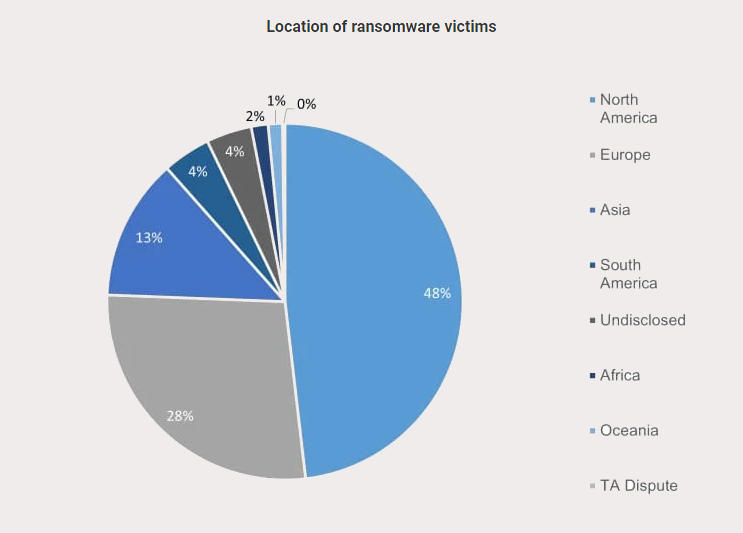
Geographically, North America emerged as the most targeted region, with 221 out of the 459 total attacks (48%). Europe followed with 126 attacks (28%) and Asia with 59 (13%). Notably, North America experienced a 96% increase in cases from February to March 2023. Conversely, Europe saw a dramatic proportional rise of 5%, signaling a potential shift in focus towards European nations during this timeframe.
Ransomware Attacks Today: Latest U.S. Companies Hit (9/13/2024) - YouTube This video provides insights into the latest ransomware incidents affecting U.S. companies and discusses implications for cybersecurity measures.
Mitigation Strategies for Cybersecurity
The report concludes by outlining several strategies to mitigate the risks associated with cyberattacks. Regularly patching vulnerabilities, maintaining offline and offsite backups, and employing endpoint security tools are essential measures for detecting exploits and malware before they can be leveraged by attackers. Additionally, staying informed about system configurations can enhance overall security posture.